A simple Checklist for Securing Your Smart Contracts

What are smart contracts and how secure are they?
Smart contracts are a type of computer code that facilitate the exchange of money, property, shares, or anything of value. They are often referred to as “programmable contracts.” Smart contracts are decentralized, meaning they are not under the control of any single party and they run on a blockchain, which is a distributed ledger.
The benefits of smart contracts include:
-Secure: Smart contracts rely on cryptography to protect them from hacking.
-Transparent: Every action taken in a smart contract is visible to all parties involved.
-They are efficient: Smart contracts can be programmed in a way that makes them easy to execute.
Key Takeaways
- Smart contracts are enabled by blockchain technology and automate contract execution and fulfillment.
- The most significant issues facing smart contracts have led to more than $4.75 billion in losses since 2012.
- A smart contract secure checklist includes following good practices, withholding access to sensitive functions, limiting the code’s complexity, testing the code for flaws, and creating a disaster recovery plan.
What Is a Smart Contract?
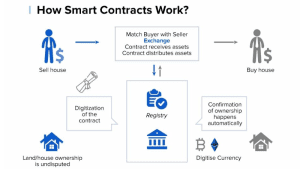
A smart contract is a set of computer code that facilitates, manages and executes the terms of an agreement. When two or more parties agree to a contract, they create a digital record of their agreement. The terms of the contract are then stored in a computer system, which can be accessed by either party at any time.
Smart contracts allow businesses to automate their contractual agreements by cutting out the middleman. This eliminates the need for third-party verification and mediation, which can save businesses time and money. Additionally, smart contracts can eliminate human error by ensuring that all agreements are automatically executed as stipulated in the contract.
How Secure Are Smart Contracts?
Smart contracts are a sophisticated innovation of conventional contract management. The nature of the terms is automatic, meaning the underlying code is immutable, so blockchain enthusiasts are drawn to smart contacts.
Unfortunately, blockchain technology is not foolproof. As recent news reports have demonstrated, there is a great deal of opportunity for fraud with blockchains and cryptocurrency, with no legal or governmental protection present. As blockchain transactions are anonymous, stolen assets are nearly impossible to locate, and subsequent losses are usually unrecoverable.
According to reports, some experts estimate that there has been a $4.75 billion loss in the collapse of unsafe smart contract systems over the past ten years. The most recent missteps, such as Godis s $615 million theft and Cypherium s $326 million signature check breaks, have contributed to the public disillusionment in smart contracts.
“The Ins and Outs of Smart Contract Audit Services”
As the world moves towards a more digitized economy, it is important that all transactions are processed and recorded correctly. This is where smart contracts come in- they are a type of contract that uses blockchain technology to facilitate and verify the terms of a contract. However, like any other form of technology, there is a risk associated with using them- specifically when it comes to ensuring their accuracy.
There are two main ways to smart contract audit: through code reviews and through performance audits. Code reviews involve manually reviewing the code itself for any potential issues, while performance audits look at how well the contract is performing in relation to its intended functions.
While both of these methods have their own advantages and disadvantages, ultimately it comes down to the auditor’s individual expertise and experience.
A Checklist for Smart Contract Security
Individuals or organizations interested in using smart contracts should devote the necessary effort to secure their assets. As a first step, take a minute to work through the items on this smart contact security checklist.
Follow Best Practices
The first thing you should do when creating new smart contracts is to follow the guidance regarding design and blockchain best practices. These might not be immediately obvious to contract specialists, but developers should be aware of them. These best practices include:
- Ensure that your development platform is stable and safe for coding, testing, and submission.
- Store all code in a secure version control system.
- Make all code modifications by means of pull requests and make sure that all pull requests have at least one independent reviewer.
- Verify that all code compiles without errors
- Thoroughly document all contract code
Limit Access to Key Functions
There are various smart contract functions that are open to the public, but this is a hazard because exposing the functions lets hackers conduct unauthorized tasks, such as the electronic forging of invoices. A safer approach is to limit access to crucial functions, so only authorized accounts can have access. This type of role-based access control is an effective method of keeping unauthorized individuals from accessing sensitive data.
Use Appropriate Function Statements
Smart contracts contain many lines of code, each with a specified purpose. Security improves when utilizing function statements to prevent sophisticated contract operations. In particular, you can make use of the following statements to undo undesirable changes and revert the smart contract program to a previous state:
- require()
- assert()
- revert()
Minimize Code Complexity
The more complicated your smart contract code becomes, the more likely it is to contain errors or vulnerabilities. Make sure to keep your smart contract code simple. Use reliable existing ones whenever you appreciate the capability to do so and do not repeat yourself by keeping major logic across multiple contracts.
Test the Code
Don’t assume that a smart contract will operate as intended. Always test your code for quality assurance, and verify that rub no unforeseen outcomes. It’s advisable to test your smart contract in small portions before finalizing it.
Conduct an Independent Code Review
For added security, commission an independent review of your smart contract code. Use a third party to analyze the code and hunt for potential flaws. You can also set up a vulnerability bounty program to encourage goodwill hackers to find the vulnerabilities in your contract code.
Guard Against Common Vulnerabilities
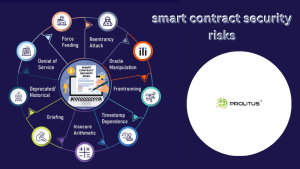
Make sure you protect your smart contracts from a number of common vulnerabilities. You could consider some of those vulnerabilities to be:
- Insecure arithmetic
- Griefing
- Deprecated/historical vulnerabilities
- Denial of service (DOS) attacks
- Force-feeding
- Reentrancy attacks
- Oracle manipulation
- Frontrunning
- Timestamp dependence
Preparing against these vulnerabilities requires the proper training and support. A smart contract security kit includes visualization, classification, static and dynamic analysis, and testing tools. It’s also helpful to periodically conduct audits of your smart contract security with these vulnerabilities in mind.
Develop a Disaster Recovery Plan
What do you do in case of a smart contract breach? In the final location on the checklist to protect against smart contract breaches, you need to develop a plan for disaster recovery.
The following elements should be included in a disaster recovery plan:
-
Event monitoring:
By tracking and recording contract events, you can track events of contract functions and identify changes to important variables. This overview notifies you when another party has finished a critical action, such as withdrawing funds and lets you discover malicious actions more quickly. Proper monitoring will allow you to respond quickly to any attacks and breaches, and you can take the necessary steps to resolve the damages and mitigate their effects.
-
Emergency stops:
If an error or unanticipated situation develops or if your team discovers flaws in the code, you need to have a team member successfully fix the code. Unfortunately, you’ll have to make this service call and detain vulnerable contract codes only during the halt phase of your disaster recovery plan. These functions permit you to modify and troubleshoot your code to troubleshoot any issues that have arisen.
-
Contract upgrades:
While blockchain contracts theoretically cannot be changed, you can add upgrade patterns within the code to delete any serious problems you identify. Upgrading on a regular basis often requires so-called proxy patterns, which rely on 2 contracts. The account interacts with a proxy contract, which refers to a separate logic contract. Upgrading a contract without modifying the code of a proxy contract happens when deploying a new logic contract.
Final Words: For Ultimate Contract Security, Contact Prolitus Technologies
Prolitus is the perfect partner for ultimate contract security. Our proprietary software and services help organizations protect their most important assets- their contracts. We offer a comprehensive suite of security solutions that include:
- Detection and analysis of contract threats
- Advanced threat detection and prevention
- Active monitoring and management of contract security posture
- Rapid response to any potential breach or attack





